Glympse is a journey sharing and location tracking application that helps either individual users or enterprise partners with deliveries and other trips. The Glympse website suggests that their userbase includes over 200k+ mobile worker devices, over 30M+ consumer devices and the Glympse android app has had around 5 million downloads.
On any given day, primarily in the United States, Glympse shares the exact routes of many individuals as well as delivery information, package details, driver information and whatever other information or metadata their enterprise partners wish to attach to their trips. Understandably, this information makes life easier for drivers as well as package recipients.
As you can imagine, much of this information is intended to be private and was given to Glympse (or an enterprise partner) on the understanding that it would be adequately protected and not publicly available. If these protections are not in place then there is potential that this information, either aggregated or in isolation, could be hugely useful to a social engineer or competitor. I think a phishing email containing real delivery and package information would be very convincing! I’m less confident that Pizza Hut would like to know Papa John’s most popular pizza, but you never know!
The Application
For the individual user, the UI is fairly simple and what you might expect of an application of this kind.
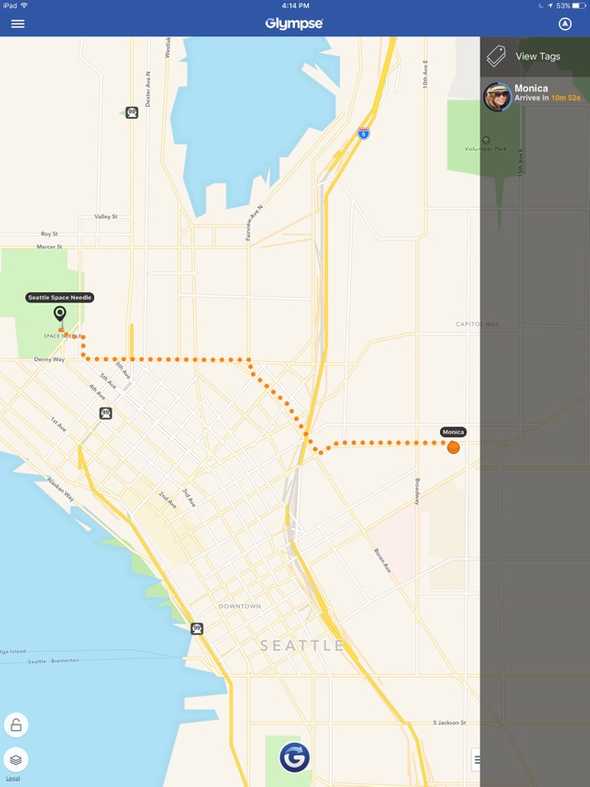
This image was taken from Glympse’s website and as you can see there isn’t anything hugely compromising and only a first name is available. You have a start location, an end location, a route and some timing information. In this instance, “Monica” is walking to the Seattle Space Needle and it is going to take her about 11 minutes. All useful information she might share with a friend she is meeting (Monica is a dummy account just in case you were wondering).
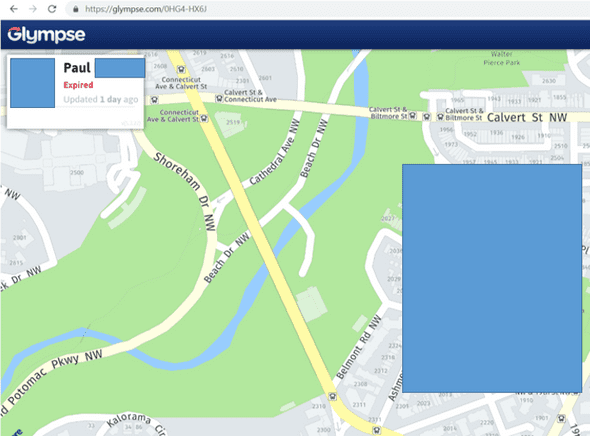
However, here is another example. I have hidden the last name, profile image and exact end location but you can see how this is potentially more problematic (the link is no longer live before you try!). Identifying an individual who has ended their trip at a home address (or residential location) is a breach of privacy and this information starts to become useful to criminals - if not cyberattackers then at the very least opportunistic burglars!
The eagle-eyed amongst you might see where this is going.
The URL (https://glympse.com/0HG4-HX6J) has a fairly short unique identifier appended on the end. 0HG4-HX6J has 9 characters and uses uppercase, special and numerical characters.
By way of comparison, most online sharefile software that generate random URLs often have upwards of 20 characters; inclusive of uppercase, lowercase, numbers and special characters (Aj5ye&hsk8Pq@3Hh%#3Q), which is many magnitudes harder to brute force or guess.
Using a Python script to generate alphanumerical codes 9 characters in length, and check if they are valid by firing an HTTP request to Glympse was initially sluggish. Even though it is a comparatively short URL ID there are still around 2 * 10^16 combinations to get through – slow progress if you need to remain below the threshold of any potential rate limiters.
However, after playing around with the app I identified a pattern! All the URL suffixes started with a zero, had a hyphen as the 5th character and no other special charachters which reduces the combination space significantly (to approximately 9 * 10^10).
A few tweaks to the Python script and it was possible to harvest thousands of valid URLs in just a few hours. This included many trips where the Glympse application had been white labelled by their enterprise partners!
Papa John’s
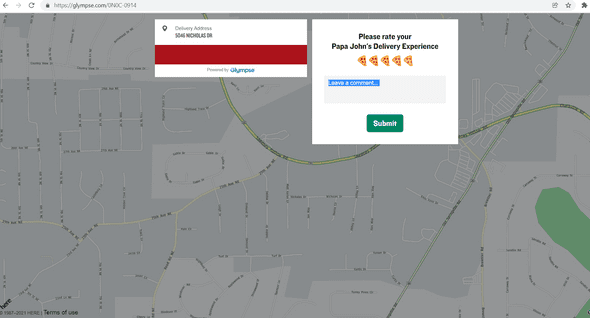
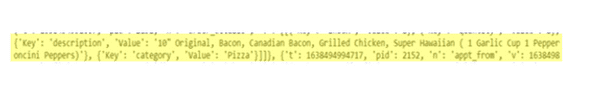
Many of the URLs which resolved to a trip were Papa John’s pizza deliveries. The HTTP response included information about with which items had been ordered, an address and in some responses, a name and telephone number (unclear if that is the driver or the recipient). There was also the option to leave a review for some of the trips which could potentially be abused if it is available for people other than the customer (Pizza Hut sponsored data pollution attack??)
Pottery Barn
Some of the URLs resolved to Pottery Barn deliveries. The data which could be captured from HTTP responses included addresses, recipient first and last names and the time of delivery. As discussed, specific information like this could be used in a convincing phishing attack. In the European Union this information would also be considered personal information under GDPR.
Tru Green
Some of the URLs resolved to scheduled lawn maintenance jobs. The data which could be captured from HTTP response included addresses and the time of the scheduled work.
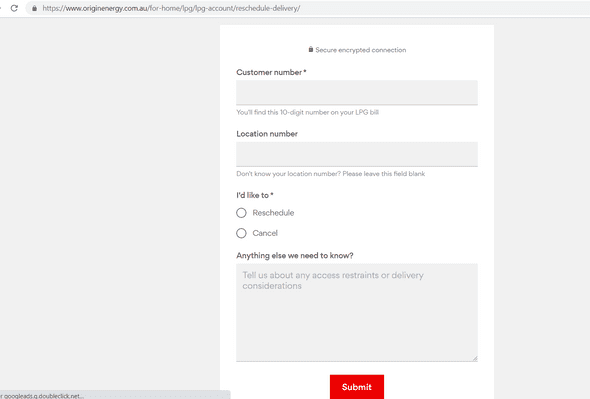
Origin Energy
Times and locations of LPG pickups and exchanges were available. Customer numbers in the HTTP response could be used on the origin website to apply for delivery rescheduling. I didn’t attempt to reschedule but the cost of heating in the UK has gone up since I first came across this information at the end of 2021!
The Fix
I wouldn’t classify this a bug or a security flaw, per se, but these were the recommndations I initially passed to Glympse when I privately disclosed it to them on 19th December 2021. These are also factors to consider should you be involved developing an app that is sharing information via a dynamically generated URL.
- Consider more aggressive rate limiting and banning IP addresses which are querying multiple different trips. Difficult when most mobile devices are behind CG-NAT.
- If there isn’t a monitoring solution in place for the trips endpoint, consider using one. Again, CG-NAT devices makes identifying patterns of abuse more difficult.
- To protect future URLs increase the URL suffix complexity by increasing the length and/or including upper/lower/special characters.
- Consider removing personally identifiable information from the front end as well as any other superfluous data.
Disclosure
I have been in contact with the Glympse Team since December 2021 assisting them with their fix and my attack is now not possible thanks to improvements that Glympse have made! Some of you may think that the fix took a while to implement and that data was exposed for too long but I understand that Glympse has a relatively small team and I was informed by members of the C-Suite that this fix was prioritised ahead of fee earning activity.
- Dec 2021 — Research conducted and private disclosure made.
- Jan 2022 — Well thought out initial response from Glympse. There were some other un-noteworthy minor findings in the viewer data flow including some publicly facing credentials in the browser app that were passed to the backend but these were intended to work as placeholders and used for logging and monitoring purposes. The URL suffix complexity was described as a larger effort, primarily due to the variety of external integrations and backwards compatibility concerns. I also turned down an offer to sign an NDA as it didn’t feel quite right before a fix was in place!
- Feb to Mar 2022 — Further discussions about rate limiting, CG-NAT, URL complexity, eliminating superfluous data and possibly password protecting trips (a decision Glympse decided against).
- Apr 2022 — Gentle nudge suggesting that < 3 months to apply a fix when personal information is publicly available is a benchmark to strive for.
- May to Jun 2022 — Glympse became a little non-responsive but I understand this was due to engineers and C-Suite holidays.
- Jul 2022 — Fix complete for individual users of the Glympse application but they wanted to wait until a large portion of their users downloaded the new latest version otherwise the fix would break the application.
- Aug 2022 — 80% of the users were on a new version of the app and the update was pushed. App now supported the newly introduced invite code (upper case, lower case, multiple hyphens and 9 characters long). Importantly, trips are “live” for a reduced amount of time and superfluous data had been minimised which made my attack obsolete. There are also future plans to increase the length of the URL suffix in line with best practice.
- Aug to Nov 2022 - Further engineering work needed to be completed to ensure the same fix was pushed to all of Glympse’s enterprise partners, there was an initial plan to publish this article on National Computer Security Day (Nov 30) but unfortunately Glypse needed more time.
- Jan 2023 - Fixes complete!
- Mar 2023 - Article published!
Side note
Another ‘lesson learned’ from this exercise is the importance of supplier due diligence and how vulnerabilities can be introduced into an organisation’s infrastructure via a supplier. Glympse are SOC 2 Type 2 certified which is one of the meatier information security accreditations. Having been employed as a consultant to assist organisations with meeting the standards and having conducted SOC 2 audits myself, it goes to show that even the most thorough best practice is fallible. An accreditation can be demonstrative of good practice (often at a point-in-time) but always strive to go above and beyond and consider vulnerabilities and security gaps that aren’t addressed by the frameworks you have adopted.
Kind Words
“Too many people in our industry use their research for their own personal gains,” said Brandon Rodgers, Senior Technical Architect, at Glympse. “We appreciate how thoughtful Dan was working with us to develop a solution that improves our platform for our customers.”